Platform
11 December 2025 CVE Florent Montel
CVE-2025-55182 / React2shell

You like this content ?
Share it on the networks
CVE-2025-55182 / React2shell→ The Land Of False Positives
Every year brings its share of security flaws, we had a blast with Fortinet, but CVE-2025-55182 and React has been in a category of its own and came as a very early Christmas Gift for all security teams around the word.
Within hours of the initial disclosure, the vulnerability had already set social networks on fire. Security Twitter was overflowing with screenshots, hot takes, “instant checkers,” and even memes. By midday, online scanners had appeared out of nowhere, and for the first time ever, we even saw browser plugins created specifically to detect a newly announced CVE (https://x.com/securityshell/status/1996976033069670548?s=20**).
That alone says a lot about the frenzy about this vulnerability.
Meanwhile, articles and press releases multiplied, and EASM solutions scrambled to explain to their customers whether they were at risk. The result: a wave of contradictory information, guesswork, and noisy alerts.
Why this vulnerability created so much confusion?
The confusion around CVE-2025-55182 started the moment people began saying that “any React app” might be at risk. That alone was enough to set the internet on fire. React is used in an enormous number of modern web applications, so thousands of developers suddenly felt concerned, whether or not the vulnerability actually applied to them.
Very quickly, GitHub and Twitter filled up with PoCs, many of them written by people who were curious but not necessarily experienced in security. Most of these scripts were based on guesswork, partial information, or misunderstandings of how the vulnerability worked. Some didn't test anything meaningful, others flagged harmless behaviors as dangerous.
As these amateur PoCs circulated, they created even more noise. Security teams received alerts, screenshots, and links from all directions, while EASM tools rushed to respond with their own (often inaccurate) detections.
In short, everyone was talking about CVE-2025-55182, but very few were actually validating anything.
How Patrowl approached the problem?
At Patrowl, we took a different route. Instead of amplifying the noise, we focused on understanding the vulnerability and on building a reliable, testable detection method.
On the same day the first technical details became public, we developed and deployed a specific exploitation module across our platform.
Not a version checker.
Not a pattern matcher.
A real, controlled test of exploitability.
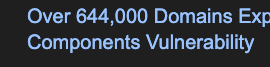
Using our automation we were able to quickly scan all our customers’ exposed assets with a high level of precision. Once deployed across our customers’ attack surfaces, the picture became much clearer:
Only a very small fraction of deployments were exploitable. As React is already a technology detected by our custom controls, targeting vulnerable component was much easier and quicker
98% of the vulnerable systems detected by Patrowl were patched within the same day, thanks to clear and unambiguous reporting.
No avalanche of false positives, no guesswork : just verified exposure.
While the rest of the ecosystem struggled to interpret the vulnerability, Patrowl customers knew exactly where they stood within the same day.
The False-Positive Epidemic
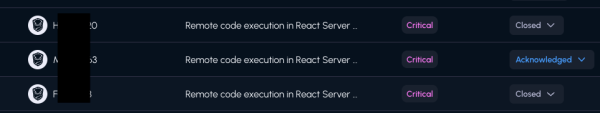
In the following days, we were contacted by companies that had been told, sometimes with alarming wording, that they were exposed to CVE-2025-55182. These alerts came from various EASM vendors relying on automated fingerprinting. In every single case, the logic behind the alert was the same: “Your React version is X, therefore you may be vulnerable.”
After manually reviewing all these alerts with the concerned organizations, the conclusion was straightforward: 100% of the reported exposures were false positives. Not one genuine vulnerability among them but a lot of time lost for everyone.
A Wake-Up Call
CVE-2025-55182 will be remembered not just for the vulnerability itself, but for the confusion it created. It exposed a deeper issue: many EASM tools still rely heavily on superficial indicators, which leads to massive false-positive storms whenever a vulnerability trends online. It obstructs companies from focusing on concrete issues in (sometimes) huge attack surfaces, making them lose focus and efficiency.
Patrowl’s approach proved that it’s possible to deliver accuracy and scale at the same time.
https://www.cert.ssi.gouv.fr/alerte/CERTFR-2025-ALE-014/
https://nvd.nist.gov/vuln/detail/CVE-2025-55182
https://react.dev/blog/2025/12/03/critical-security-vulnerability-in-react-server-components





