Platform
Rethink pentesting: continuous, clear, and controlled
Applications, websites, APIs... Patrowl reinvents external pentesting to make it truly efficient against today’s evolving threats.
Our unique solution combines continuous automation with human validation to turn every alert into clear, prioritized insights tailored to your business impact.

Detailed reports: Generate reports anytime and verify fixes instantly.
Risk-free pentests: No impact on production, even on sensitive assets.
Guaranteed expertise: Our certified pentesters (OSCP, OSWE, CEH) ensure zero false positives.
Smart prioritization: Test only what really matters — avoid overbilling and alert fatigue.
Continuous visibility: Monitor your external attack surface in real time (shadow IT, forgotten assets).
Actionable recommendations: Fix faster with expert guidance tailored to your environment.
More than 100 clients, including CAC 40 companies
A solution built by pentesters and cybersecurity auditors
Focus on what matters
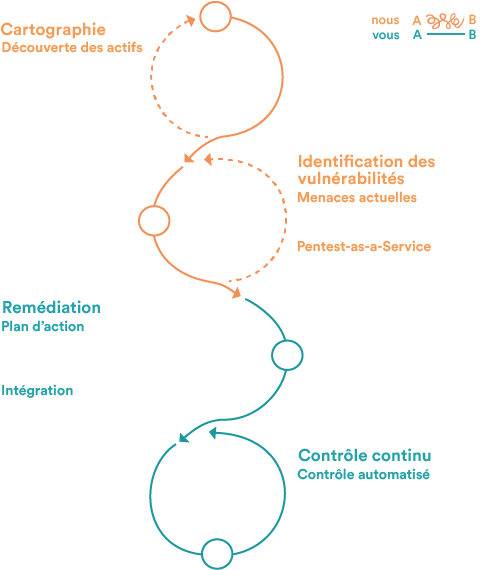
Your pentest in 4 simple steps:
We prioritize your vulnerabilities and provide concrete fixes, so you can focus on what really matters: remediation.
Dynamically map all your exposed assets, including Shadow IT
Detect vulnerabilities continuously, with human validation
Prioritize remediation with clear, actionable recommendations — integrated with your tools
Verify fix effectiveness and automate retesting
Launch the right test at the right time
Secure
your sites, apps, and APIs from the start
Verify
existing security or after major changes
Prepare
compliance audits with confidence
Respond
to client or partner security requirements
Maintain
continuous control of critical assets
Integrate
new entities or subsidiaries securely
Secure everything you expose online
With Patrowl, get full coverage of your internet-facing assets:
Web apps & websites: XSS, injections, misconfigured cookies
Open ports & services: detect exposed, misconfigured services
DNS & email: SPF, DKIM, DMARC, domain security
SSL/TLS certs: validity, configuration, weak algorithms
APIs & mobile apps: REST, GraphQL, Android/iOS testing
Exposed cloud infrastructure: web interfaces, public IPs, open buckets

Vulnerability management built for compliance
We secure your assets according to international standards and deliver expert-validated, audit-ready reports.
Regulatory standards:
DORA, NIS2, CyberScore, CaRE Program, ISO 27001
Testing frameworks:
OWASP Top 10, PTES, OSSTMM, MITRE ATT&CK, NIST 800-115
Certified experts:
SANS GIAC (GPEN, GWAPT, GXPN), OSCP, OSWE
Secure solution
Includes secure access (encryption and authentication via MFA or SSO)
Remediation and follow-up reports
Secure access (encryption, MFA & SSO)
PDF remediation reports: delivered via email
Vulnerability prioritization based on exploitability, business impact (CVSS v3.1), and application context
Remediation plan includes:
IoCs (Indicators of Compromise)
Actionable recommendations tailored to your tech stack
Standard classification (OWASP Top 10, SANS CWE)
Technical details: example payloads, business risks

The leader
How do our automated pentests work?
At Patrowl, our hybrid pentests orchestrate continuous, high-level security checks — more comprehensive than classic manual tests.

Hybrid model: fast automation + human validation = reliable results
In-house engine: developed since 2018, continuously updated with the latest tools & techniques
Daily updates: our certified pentesters continuously feed our engine with cutting-edge insights from real-world vulnerability monitoring
Always up-to-date, independent from human availability — for accurate, business-aligned results.
A trusted French solution
Grand Prix InCyber Europe (FIC) 2025
Innovation Award – Assises de la Cybersécurité
France Cybersecurity Label
Featured in Wavestone’s Cybersecurity Radar
100% customer renewal rate in 2024

Our partners
Why Patrowl?
Zero false positives
Focus only on real threats
Zero setup
Fully SaaS — no maintenance or coding required
Onboarding and support
Dedicated Customer Success
Seamless integrations
Connect to your ticketing tools via custom API
Our Offers
Anticipate attacks before they happen. Move from one-off testing to continuous security monitoring.
Advanced EASM
Take control of your attack surface.
Real-time, continuous monitoring of all exposed assets (domains, certificates, applications, emails, credentials)
Immediate detection of Shadow IT, misconfigured services, and forgotten assets
Risk-based prioritization of exposures, using active threat intelligence (CISA KEV)
Rapid reduction of your attack surface through automated, guided remediation
Full visibility into what’s publicly accessible — no blind spots, no surprises
Continuous Pentest
Automate your pentests, identify real vulnerabilities.
Real-time, dynamic mapping of your external attack surface
Automated pentests validated by certified experts — zero false positives
Continuous testing of applications, exposed services, ports, protocols, and subdomains
Prioritization of vulnerabilities based on business impact and exploitability
Expert remediation reports with clear, actionable fixes for fast response

Your most frequently asked questions
What types of vulnerabilities can Patrowl detect?
Patrowl covers the full spectrum of vulnerabilities found on your external attack surface, across three main categories:
1. Known vulnerabilities (CVE, CNNVD, etc.)
Patrowl continuously monitors public vulnerability databases (such as CVE) and alerts you as soon as a known vulnerability affects your exposed assets.
As a recognized CERT, we ensure fast and accurate detection.
2. Non-referenced or custom vulnerabilities (non-CVE)
These are the most frequent — and often the most critical.
They result from human error (misconfigurations, default access, injections, weak passwords, etc.) and are rarely published in official databases, yet widely exploited by attackers.
Patrowl identifies them using its advanced behavioral analysis engine.
3. Zero-day vulnerabilities
In some cases, our automation and expert capabilities allow us to detect zero-day vulnerabilities (not yet publicly disclosed) affecting specific products or plugins.
When this happens, Patrowl handles coordinated disclosure with the vendor and provides you with temporary mitigation measures until an official patch is released.
What types of assets does Patrowl support?
Patrowl can monitor and test a wide range of external assets, including:
IP addresses and IP subnets
Autonomous systems (AS numbers)
Domain names and DNS zones (second-level domains, subdomains)
DNS records (MX, SPF, DMARC, NS, etc.)
FQDNs, URLs, and specific web pages
Public cloud accounts (AWS, Azure, GCP, etc.)
Corporate email addresses
Custom keywords (company name, brand, product, sensitive terms, etc.)
What’s the difference between Patrowl and a traditional vulnerability scanner?
Patrowl goes far beyond a basic vulnerability scanner.
While most scanners only detect CVEs on a static perimeter and require deep technical expertise to interpret, Patrowl delivers continuous, comprehensive, and intelligent monitoring — covering:
Known vulnerabilities (CVE, OWASP, etc.)
Misconfigurations
Data leaks
Real-time, dynamic mapping of your internet exposure
Our key advantage?
Every vulnerability detected is validated by our in-house pentesters to confirm it is actually exploitable.
The result:
Zero false positives
Only relevant, business-impacting alerts
Clear, actionable remediation guidance — even for non-technical teams
How do you ensure zero false positives?
Every vulnerability reported by Patrowl goes through a rigorous multi-step qualification process:
Automated pre-qualification based on multiple criteria:
Technical severity (CVSS v3 score)
Business criticality of the asset
Exposure level of the asset
Source and context of the vulnerability
Human validation:
Each vulnerability is then reviewed and confirmed by an offensive security expert to ensure it is truly exploitable.
This hybrid approach guarantees zero false positives and ensures that every alert is relevant, actionable, and prioritized.
What are the limitations of traditional one-off penetration tests?
A penetration test simulates real-world attacks to identify security vulnerabilities. Unlike automated scanners, it is conducted by cybersecurity experts and involves in-depth analysis.
However, traditional pentests come with several key limitations:
1. Limited frequency
Usually performed once or twice a year, they can’t keep up with the fast pace of evolving threats. Gaps remain between tests, leaving systems exposed.
2. High cost
Because they rely on expert manual work, pentests are expensive — making it hard for many organizations to run them regularly.
3. Lack of follow-up
Once the final report is delivered, there is often no ongoing monitoring or validation to ensure that vulnerabilities are properly remediated.