Platform
ADVANCED EASM OFFER
EASM: External Attack Surface Management
What you unknowingly expose on the Internet can be exploited. Patrowl helps you take back control.
Continuous scanning of the web, DNS, cloud, certificates, domains, subdomains, public repositories... Patrowl automatically identifies your exposed assets and alerts you only when there is a real danger.

Alerts only for genuinely exploitable exposures
Up-to-date mapping of your environments (prod, staging, shadow IT)
100% sovereign and hosted in France – compliant with sectoral regulations
Easily integrates with your existing SIEM, SOAR, and ITSM platforms through robust APIs.
Vulnerability validation by certified pentesters (OSCP, OSWE, CEH, eJPT)
Trusted by 100+ organizations, including major CAC 40 companies
A Solution Built by Pentesters and Cybersecurity Experts
Typical Use Cases
Multiple websites or apps to secure
Secure your entire web asset inventory from the start with agile, flexible testing.
Assess the security of existing infrastructure
Get a clear, accurate view of current vulnerabilities — resolved or not.
Prepare for compliance audits
Be ready for NIS2, DORA, or CaRE programs with traceable, exportable reports.
Continuous security monitoring
Close the visibility gap left by scanners, bug bounties, or Red Teaming.
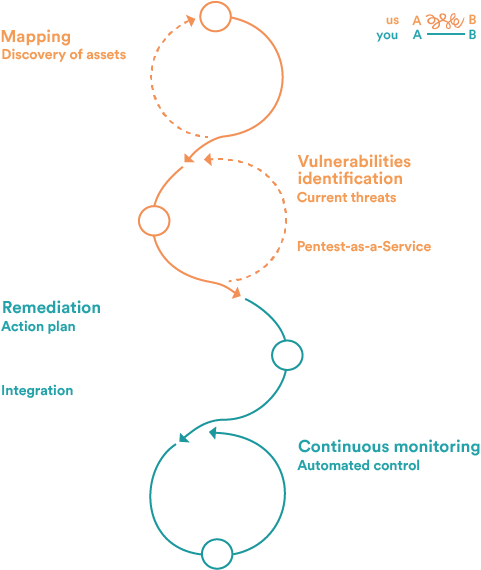
Steps
4 Steps to Continuous Risk Control
Automatic Asset Mapping
→ Instantly identify exposed assets (shadow IT, websites, apps, third parties…).Active and Passive Vulnerability Detection
→ Discover known and unknown flaws, enriched with threat intel and validated by our CERT.Prioritized Remediation
→ Focus on what matters with contextualized, actionable remediation plans integrated into your tools.Continuous Control
→ Track remediation effectiveness with retests, continuous monitoring, and on-demand reporting.
Features That Solve Real Problems

Take control of your external attack surface
Common pain points:
→ Lack of visibility on exposed assets (including third-party, shadow IT, brand impersonation…)
Key capabilities:
Certificate checks (expiration, TLS, cryptography)
Web app analysis (WAF, CDN, bypass techniques)
Email security (SPF, DKIM, DMARC, DNSSEC, reverse DNS)
Detection of leaked credentials (public files, Pastebin, etc.)
Exposure of services (admin panels, ports, databases, backdoors)
Real-time change detection on exposed assets

Prioritize based on active threats, not static lists
Problem: Too many vulnerabilities, not enough clarity on what really matters.
Key capabilities:
CISA KEV + real exposure correlation
Enriched scoring: public exploit available, active use in the wild, business impact
Detection of unknown or misconfigured vulnerabilities
Patrowl CERT: human qualification + private threat intelligence

Smarter CVE Management
Problem: Legacy tools list thousands of CVEs but don’t help prioritize.
Key capabilities:
Automatic tech ↔ CVE correlation
Risk enrichment (KEV, public exploit, EPSS)
Agentless scanning (web, API, protocols)
Sorting by exposed technology and impacted asset

Anticipate risks from exposed technologies
Key capabilities:
Passive stack scanning (product, version, vendor)
No agent or manual config needed
CVE correlation from exposure
Enriched technical documentation

Generate audit-ready, actionable reports in one click
Key capabilities:
Comprehensive exportable PDF reports
Filtering by severity, tech, exploitability, standards
Detailed remediation plan with IoCs
OWASP / CWE / SANS classifications
Built-in payloads and exploitation scenarios

Seamless integration into your tools and workflows
Key capabilities:
Automatic ticket creation (ServiceNow, Jira, GLPI)
Real-time alerts via email, Slack, Teams
Multi-entity support (groups, BUs, clients, projects)
Bi-directional sync for remediation follow-up
Benefits:
Scalable, trackable remediation
Cyber governance adapted to complex orgs
Frictionless integration with business tools

Ensure vulnerabilities are properly fixed
Key capabilities:
35+ families of automated retests
Standardized results (CVE, CWE, OWASP, CPE)
Scan execution tracking per asset or group
Full remediation history







WHY PATROWL.IO?
0 false positives:
Let your teams focus on real, qualified threats
SaaS simplicity:
No maintenance, no client-side configuration
0 setup:
Go live in under 30 minutes
24/7/365 availability:
Secured access with encryption and MFA/SSO
Improvement:
Continuous service monitoring & quality evolution
Patrowl: Trusted, Recognized, Sovereign Cybersecurity
100% French solution – France Cyber Security certified
Startup Grand Prize – Forum InCyber Europe (FIC) 2025
Innovation Award – Assises de la Cybersécurité 2022 & 2023
Featured in Wavestone’s FR & UK Cyber Radar
100% customer renewal rate in 2024

Our Partners
Our Offers
Anticipate attacks before they happen. Move from one-off testing to continuous security monitoring.
Advanced EASM
Take control of your attack surface.
Real-time, continuous monitoring of all exposed assets (domains, certificates, applications, emails, credentials)
Immediate detection of Shadow IT, misconfigured services, and forgotten assets
Risk-based prioritization of exposures, using active threat intelligence (CISA KEV)
Rapid reduction of your attack surface through automated, guided remediation
Full visibility into what’s publicly accessible — no blind spots, no surprises
Continuous Pentest
Automate your pentests, identify real vulnerabilities.
Real-time, dynamic mapping of your external attack surface
Automated pentests validated by certified experts — zero false positives
Continuous testing of applications, exposed services, ports, protocols, and subdomains
Prioritization of vulnerabilities based on business impact and exploitability
Expert remediation reports with clear, actionable fixes for fast response

FAQ
What is External Attack Surface Management (EASM)?
External Attack Surface Management (EASM) is an emerging concept that enables organizations to continuously discover, identify, and assess all Internet-facing assets that could be compromised or leak data if misconfigured, unmanaged, or unpatched.
When not performed continuously, EASM may also be referred to as RECON, digital fingerprinting, or digital footprint mapping.
We don’t sell EASM as a standalone solution — it is the first step of our PTaaS (Pentest-as-a-Service) offering.
Why Invest in External Attack Surface Management (EASM)?
External Attack Surface Management (EASM) provides you with a continuously updated view of your Internet-facing assets and the cybersecurity risks they expose.
“If you know the enemy and know yourself, you need not fear the result of a hundred battles.
If you know yourself but not the enemy, for every victory gained you will also suffer a defeat.
If you know neither the enemy nor yourself, you will succumb in every battle.”
— Sun Tzu, The Art of War
What types of assets does Patrowl support?
Patrowl can monitor and test the following types of assets:
IP addresses and IP subnets
Autonomous Systems (AS)
Domain names and DNS zones (second-level domains, subdomains)
DNS records (MX, SPF, DMARC, NS, etc.)
FQDNs, URLs, and specific web pages
Public cloud accounts (AWS, Azure, GCP, etc.)
Corporate email addresses
Custom keywords (company name, brand, product, formula…)
What’s the difference between Patrowl and a traditional vulnerability scanner?
Patrowl goes far beyond a standard vulnerability scanner. While traditional tools are limited to detecting CVEs on a fixed perimeter and require significant expertise to interpret, Patrowl automates continuous, comprehensive, and intelligent monitoring — including vulnerabilities (CVE, OWASP, etc.), misconfigurations, data leaks, and a dynamic mapping of your Internet exposure.
Our key advantage: internal pentesters manually validate each detected vulnerability to confirm it is truly exploitable.
Result: zero false positives, and only relevant, actionable alerts — with detailed, tailored remediation guidance.