A recently identified vulnerability, CVE-2025-29927, affects the Next.js framework, a popular choice for building React-based web applications. This critical security flaw, assigned a CVSS score of 9.1, enables attackers to bypass authorization mechanisms implemented via Next.js middleware, potentially granting unauthorized access to sensitive resources.
This vulnerability impacts the following Next.js : Versions from 11.1.4 through 13.5.6, 14.x before 14.2.25, and 15.x before 15.2.3 are vulnerable.
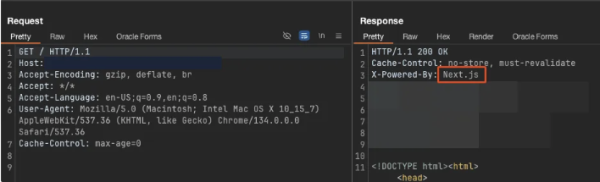
The root cause of this issue lies in the handling of the x-middleware-subrequest header by Next.js.
This header is internally used by Next.js to prevent infinite request loops.
Attackers can manipulate this header to bypass security middleware, allowing requests to reach protected routes without proper authorization checks.
By injecting this header into a malicious request, an attacker can exploit the system's reliance on middleware-based authorization.
However, identifying and verifying this vulnerability can be particularly tricky.
Why? Because the vulnerability only affects applications that rely solely on middleware-based authorization. This is a very specific configuration from developer or system operators. Most of all, If additional security layers are in place, the exploit may not be immediately visible.
To detect the real exploitability of the vulnerability, a deep understanding of the application and how it has been built is needed. The specific configuration and installation of all NextJS framework needs to be analyzed, the detection of pages protected by NextJS security mechanism needs to be automated, and all results need to be analyzed with accuracy.
This, of course, cannot be performed by classic security scanners, EASM or ratings solutions. This only could be done in one shot by a Pentester or Hunters. Patrowl is the only solution allowing our customers to check this vulnerability at scale, with precision, on all your assets exposed continuously!
To identify vulnerable applications, we relied on a funnel approach:
Exclude applications not using the Next.js framework
Exclude applications running on a non-vulnerable version
Extensively crawl the remaining applications to find endpoints
Test exploitation payloads on these endpoints
Trying to skip the first steps and trying to send payloads on random paths on every single application we monitored would be infeasible, very verbose and inefficient.