Platform
DAST : Dynamic Application Security Testing
Protect your applications and websites with the only 100% French solution that continuously detects and validates vulnerabilities, with zero false positives, and alerts you only when your assets are truly exposed.

Detailed reports on demand to track fixes and document your audits
Non-intrusive testing with zero impact on production, even in critical environments
Certified expertise: OSCP, OSWE, CEH – zero false positives guaranteed
Smart prioritization of truly exploitable vulnerabilities
Real-time visibility on your external attack surface (Shadow IT, forgotten assets)
Why should you regularly test the security of your web applications?
With the rise of the cloud, microservices, and rapid DevSecOps cycles, modern applications are a primary target for attackers. Application security testing is no longer optional. A misconfigured endpoint, an injection SQL vulnerability, or a flawed authentication flow is enough to compromise critical assets.
Patrowl’s DAST solution simulates real-world attacks (black box test approach) to detect vulnerabilities in your running application, without requiring access to source code. Unlike static application security testing, which only scans code, our DAST scanner tests behavior in real-world conditions, ensuring accurate results — not guesses.
Our dynamic security testing process actively finds vulnerabilities that matter, prioritizes them based on real exploitability, and integrates seamlessly into your tools and workflows.

Two complementary DAST solutions
Continuous DAST scans + EASM
Automate the security of your applications with real-time visibility on your external attack surface.
Continuous DAST scans of web applications, APIs, and exposed interfaces
Detection of known vulnerabilities (CVE, CWE) and advanced threats (OWASP Top 10)
EASM (External Attack Surface Management) to uncover shadow IT
Contextual technical recommendations based on real risks
Seamless integration with security tools like Jira, ServiceNow, GLPI
Auto re-testing after remediation
Ideal for proactive production environment monitoring or DevSecOps pipelines
Hybrid Pentest (Automated + Manual)
For high-stakes environments, combine automation and human expertise in a complete black box DAST test.
Simulated attacks run in black box mode, no source code required
Follows industry standards: PTES, OSSTMM
Detection of complex or non-signature-based vulnerabilities
Manual validation by certified experts (OSCP, OSWE, CEH, GPEN, GWAPT)
Full report including exploitation proofs, risk analysis, and actionable fixes
Manual and automated re-tests post-remediation
Compliance-ready: DORA, NIS2, CyberScore
Core Features & Security Testing Process

Regain control of your attack surface
TLS certificate validation (expiry, cipher strength)
WAF/CDN detection and bypass analysis
DNS and email security checks (SPF, DKIM, DMARC, Reverse DNS)
Leaked credentials detection (pastebin, breach monitoring)
Discovery of risky services: admin panels, exposed databases, backdoors
Real-time change detection
→ Benefits: full visibility, regulatory compliance (RGPD/NIS2/DORA), and third-party security validation

Prioritize according to real-world threats
Auto-correlation with CISA KEV and EPSS scoring
Detection of live, weaponized exploits
Advanced logic to detect injection SQL and other critical flaws
Continuous threat intelligence via Patrowl’s internal CERT team
→ Benefits: time savings, reduced noise, focus on actual threats

Smarter CVE Management
CVE-to-technology mapping
Business-context filtering
Real-time enrichment based on exploitability
Passive scanning of web, APIs, and protocol layers
→ Benefits: fewer false positives, clearer risk picture, immediate compliance

Proactively manage exposed technologies
Automatic fingerprinting of tech stacks (products, versions)
No manual configuration needed
Mapped to known vulnerabilities
Auto-generated technical documentation
→ Benefits: anticipate obsolescence, control exposures, simplify audits

Export clean, audit-ready reports
Complete, exportable PDF reports
Sorting by criticality, technology, and standard (OWASP, CWE, SANS)
Includes IoCs and real payloads used during testing
→ Benefits: clean stakeholder communication, no manual formatting needed

Integrate with your existing security tools
Native ITSM connectors: Jira, ServiceNow, GLPI
Alerts via Slack, Teams, Email
Multi-tenant support for MSSPs or large groups
Full two-way ticket sync
→ Benefits: unified governance, automated remediation workflows, enterprise scalability

Ensure vulnerabilities are really fixed
Automatic re-testing post-remediation
Track by asset or group
Full history of remediation status
30+ families of standardized tests (CVE, CWE, OWASP)
→ Benefits: full traceability, audit readiness, peace of mind







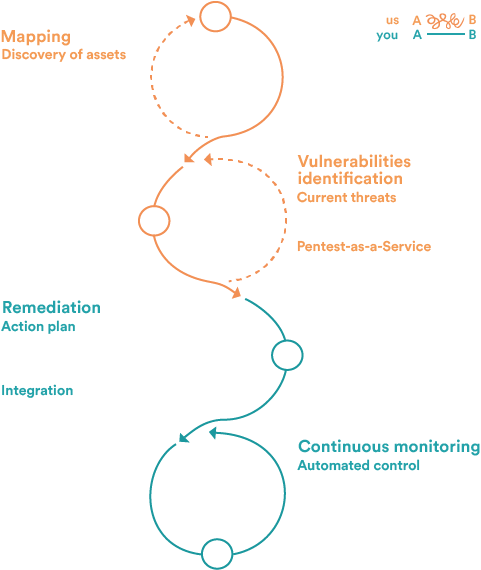
Vulnerability Management in 4 Steps
Automated asset mapping
Identify your exposed assets (shadow IT, websites, apps, third parties…) to avoid any blind spots.Active and passive detection
Find known and unknown vulnerabilities, validated by our CERT and enriched with threat intelligence.Prioritized remediation
Receive a clear, ranked action plan that integrates directly into your ITSM tools.Continuous monitoring
Ensure fixes are effective through automated re-tests and reporting.
What makes our platform stand out?
0 false positives
Focus only on real, validated risks and vulnerabilities.
0 configuration
Fast and easy deployment — up and running in about 30 minutes.
24/7/365
Secure access with encryption and MFA/SSO authentication.
SaaS solution
No maintenance or client-side development required.
100% renewal rate in 2024
A trusted platform with proven customer satisfaction.
Flexible pricing
Scalable plans with volume discounts and unlimited users at no extra cost.
Automation without sacrificing expertise
At Patrowl, automation is powered by human expertise.
Our internal pentesters model the best detection strategies, which we then automate to maximize coverage. Each vulnerability is validated by our CERT team to ensure reliability and remove noise.


Frequently Asked Questions About Our Solution
What vulnerabilities does Patrowl’s DAST solution detect?
✔️ Critical vulnerabilities:
SQL Injection (SQLi)
Cross-Site Scripting (XSS)
Authentication bypasses
Misconfigured SSL/TLS
Insecure file uploads
Exposed ports and services
✔️ Non-intrusive analysis
✔️ Real-time detection
✔️ Reliable and actionable results
Do you need access to the source code?
No — Patrowl operates in black box mode. No access to source code is required.
DAST, SAST, IAST — What’s the difference?
SAST (Static Application Security Testing):
Static code analysis using a white-box approach, typically used by developers during development.DAST (Dynamic Application Security Testing):
Dynamic testing in real execution environments using a black box approach, without access to source code.IAST (Interactive Application Security Testing):
Combines SAST and DAST through installed agents. More complex to deploy but provides deeper insights.
Each approach is complementary, depending on the phase: development, testing, or production.
How long does it take to get started?
Less than 30 minutes. No heavy deployment or agents required.
Can I export the results?
Yes — as clear, detailed PDF reports, sorted by severity or by standard (e.g. OWASP, CWE).