Platform
N°1 OFFENSIVE SECURITY AS A SERVICE
CERT (Computer Emergency Response Team)
Security incident response for active protection of your systems
An attack can compromise everything. The question is no longer if, but when. Every second counts. That's where CERT (Computer Emergency Response Team) comes in. It's your dedicated security incident response team. It also strategically protects your systems.
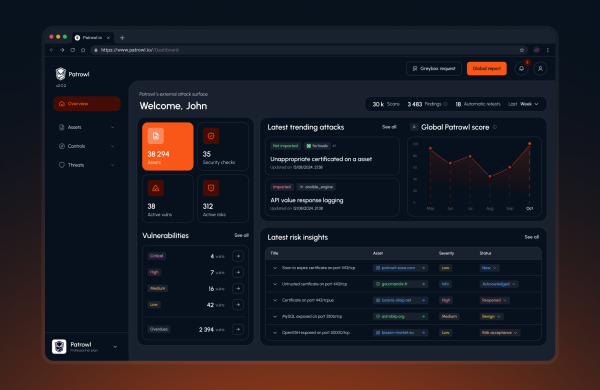
An essential bulwark against cyber attacks
A CERT is an elite team specialized in cybersecurity, capable of :
Detect cyberthreats in real time
Respond immediately to critical incidents
Coordinate IT crisis management
Prevent future attacks through a proactive approach
Also known as CSIRT (Computer Security Incident Response Team), CERT acts as a true cyber command center, in liaison with other security components such as the SOC (Security Operations Center).

Patrowl: the offensive defense tool and solution for CERTs
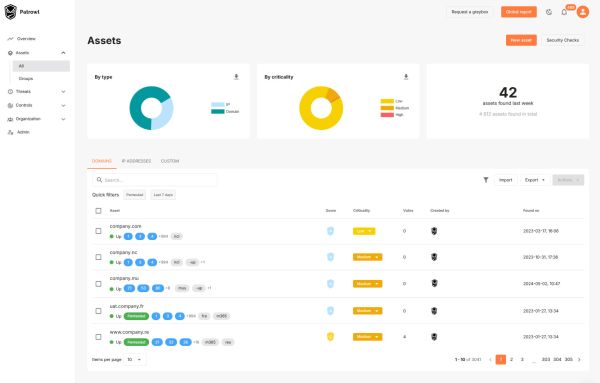
Continuous detection, no false positives
Continuous automated pentests (black-box), coupled with advanced scenarios.
Identification of known (CVE) and unknown (OWASP, PTES, OSSTMM) vulnerabilities.
Zero unnecessary alert overload: all data is contextualized and qualified.

Comprehensive asset mapping and monitoring
Detection of Shadow IT, often responsible for critical breaches.
Full visibility of exposed assets and evolution of the attack surface.
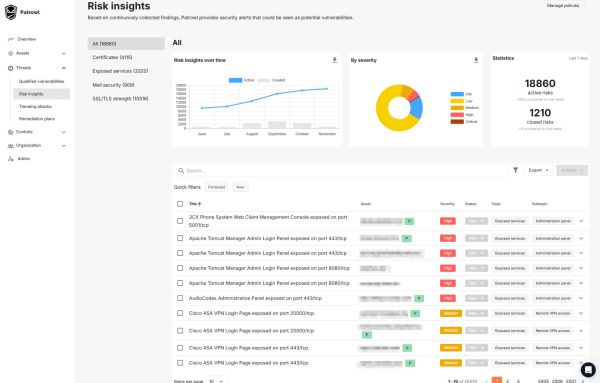
Prioritization based on real risk
Intelligent sorting by CVSS, EPSS, business criticality.
High-impact vulnerabilities are immediately highlighted for rapid treatment.



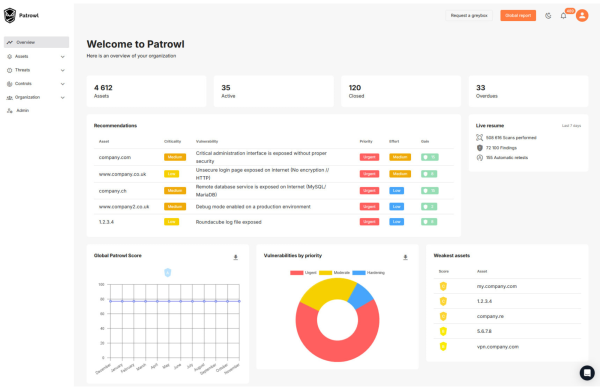
Patrowl's advantages on the market
0 false positive
to enable cybersecurity teams to focus on qualified risks and vulnerabilities
Simplicity
Saas without maintenance or client-side programming
0 setup
with quick and easy commissioning in just 30 minutes
24/7/365
Including secure access (encryption and MFA or SSO authentication)
Follow-up
Service operations and quality improvement
Compliance and cyber audits at your fingertips
Patrowl helps you to meet the requirements of all major standards. Instant export of reports in PDF, JSON or CSV format, with full digital forensic and documented crisis communication.
NIS 2
Critical infrastructure cybersecurity
DORA compliance
Resilience for financial institutions
CyberScore
Cyber rating in France
CaRE program
State aid for healthcare facilities
FAQ
CERT vs CSIRT vs SOC: what's the difference?
The concepts of CERT, CSIRT and SOC are often associated with the response to computer attacks, but they are distinguished by their specific roles:
CERT
Computer Emergency Response Team: Usually operates on a large scale, often at national or sector level, focusing on managing cybersecurity incidents and thinking proactively to prevent cyberattacks. It stands out for its strategic and comprehensive prevention approach.
CSIRT
Computer Security Incident Response Team:Operates within organizations, with a focus on incident response to limit damage. More focused than CERT, it aims to react quickly and effectively to security incidents, in order to minimize their impact.
SOC
Security Operations Center: A continuous monitoring center for security incidents for a specific organization, the SOC supervises threats in real time, with advanced technologies to detect, analyze and respond to threats before they become major incidents. The SOC is often the first line of operational defense.