Platform
Why is it so hard to prioritize CVEs?
Every year, over 40,000 new vulnerabilities (CVEs) are published, growing by 30% annually. Nearly 40% are actively exploited within 6 months – impossible to handle manually.
A CVE (Common Vulnerabilities and Exposures) is just a standard identifier (e.g., CVE‑2025‑12345). It tells you a flaw exists, but not whether you are exposed, if the flaw is actively exploited, or its real impact on your assets.
Too much noise:
most CVEs don’t apply to your environment.
Lack of context:
raw CVSS scores don’t reflect business reality.
Constant urgency:
you must choose between critical patches, false positives, and active threats.
A solution built by pentesters
The leader in vulnerability management
Finally, CVE management that is clear, actionable, and useful.
Patrowl cuts through the noise and keeps only the vulnerabilities that truly matter to you.

Clear view of your exposure: detect visible assets and technologies that are truly vulnerable.
Contextual prioritization: focus on critical, exploitable, and active flaws.
Targeted alerts: receive only CVEs relevant to your environment.
Simplified operations: integrate alerts directly into your ITSM tools or API, with automatic verification after remediation.
Smart vulnerability prioritization
Accounts for real exploitability (required privileges, complexity, user interaction).
Detects actively exploited flaws and public exploits (GitHub, Exploit‑DB, underground forums).
Immediate alerts for critical vulnerabilities (CISA KEV, major media coverage)
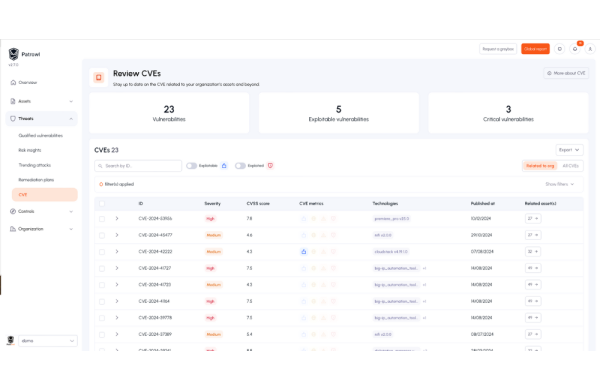
Operational context for every CVE
Criticality adapted to your organization, beyond raw scoring.
Clear identification of exposed assets with real evidence of exposure.
Automatic detection of frameworks, OS, servers, and technologies.
Extra details to plan remediation: publication date, affected product.
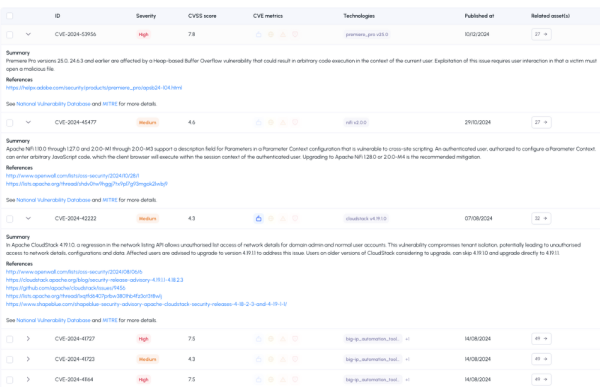
Advanced filtering to cut the noise
“Related to Org” view: only vulnerabilities tied to your assets.
“All CVEs” view: for proactive global monitoring.
Custom filters by severity, exploitability, technology, product, or date.
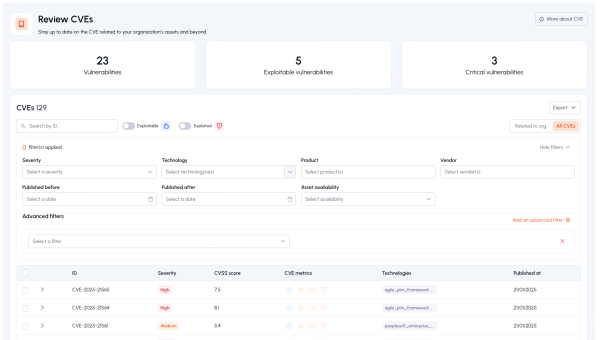
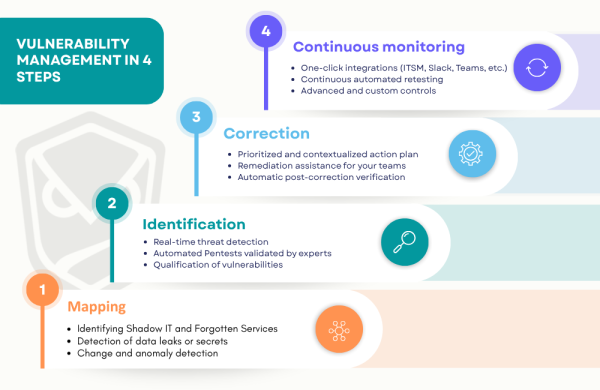
Simplified vulnerability management
Automatic mapping of exposed assets (Shadow IT, third parties, subdomains).
Active & passive detection via scans, Threat Intelligence, and Patrowl CERT.
Prioritized remediation based on severity, exploitability, and exposure.
Continuous monitoring with auto‑verification of fixes and exportable reports.
Automation meets human expertise
At Patrowl, we believe no machine can replace an expert’s judgment, but experts should never waste time on what machines can automate.

Real‑time monitoring & automated detection: our CERT continuously tracks CVEs, exploits, and APTs, deploying checks as soon as risks emerge.
Pentesters who code: every validated manual technique is industrialized for reliable detection.
Human review on every alert: all vulnerabilities are verified and prioritized by our experts.
Result: zero false positives, 100% actionable.
Advantages
Why Patrowl.io?
0 false positives
only real, prioritized vulnerabilities.
Simplicity
SaaS with no maintenance or coding required.
Zero setup
live in 30 minutes.
24/7/365
secured access with encryption & MFA/SSO.
100%
customer satisfaction in 2024.
+40%
rediscovery of your external attack surface with Patrowl.
Our Partnership
Our Offers
Anticipate attacks before they happen. Move from one-off testing to continuous security monitoring.
Advanced EASM
Take control of your attack surface.
Real-time, continuous monitoring of all exposed assets (domains, certificates, applications, emails, credentials)
Immediate detection of Shadow IT, misconfigured services, and forgotten assets
Risk-based prioritization of exposures, using active threat intelligence (CISA KEV)
Rapid reduction of your attack surface through automated, guided remediation
Full visibility into what’s publicly accessible — no blind spots, no surprises
Continuous Pentest
Automate your pentests, identify real vulnerabilities.
Real-time, dynamic mapping of your external attack surface
Automated pentests validated by certified experts — zero false positives
Continuous testing of applications, exposed services, ports, protocols, and subdomains
Prioritization of vulnerabilities based on business impact and exploitability
Expert remediation reports with clear, actionable fixes for fast response

FAQ
How does Patrowl qualify CVEs?
We combine automated analysis with human validation. Criteria include technical severity (CVSSv3), asset importance, and real exploitability (POC, public exploit, active usage).
Are you alerted to new critical CVEs?
Yes. Our CERT team and monitoring platform detect them in real time.
Specific checks are immediately developed and deployed to your assets to verify exposure.
Can I organize my assets automatically?
Yes. Patrowl automatically maps and updates your exposed assets, including Shadow IT and third‑party services.