Platform
Features
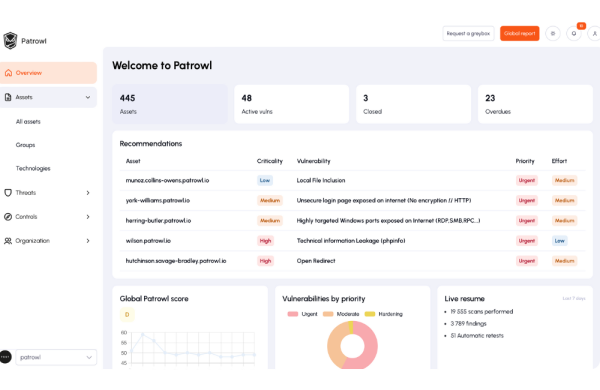
Turn our IT Asset Inventory & Discovery into a security advantage
Understanding what’s exposed online is the first step to staying secure. Patrowl makes it simple: we turn your asset inventory into a powerful, easy-to-manage tool for reducing risk — without complexity.
Built by offensive security experts
Why is asset discovery crucial?
Every resource exposed on the Internet represents an opportunity for an attacker. Yet, most organizations do not have a complete mapping of their IP addresses, domain names, public APIs, or externally accessible applications.
The result: silent vulnerabilities, incomplete audits, and compliance that is difficult to maintain.
Shadow IT
and undeclared projects: new websites, applications, or initiatives launched without security validation.
Forgotten
or orphaned assets: virtual machines, legacy websites, or APIs that are no longer maintained but remain accessible.
Expanded attack surface
through subsidiaries and providers: services exposed outside the official security perimeter.
Compliance
and vulnerability prioritization: incomplete inventories distort audits and hinder effective remediation.
Regain Control of Your External Attack Surface

Automatically Discover Exposed Assets
What it does:
Continuously scans for internet-facing domains, subdomains, IPs, ports, services, TLS certificates, and virtual machines.
What you get:
- A complete, up-to-date map of your attack surface — even across cloud and hybrid environments
- Identification of unknown assets and unmanaged services
- Real-time updates to reflect CI/CD changes, M&A activity, or new deployments

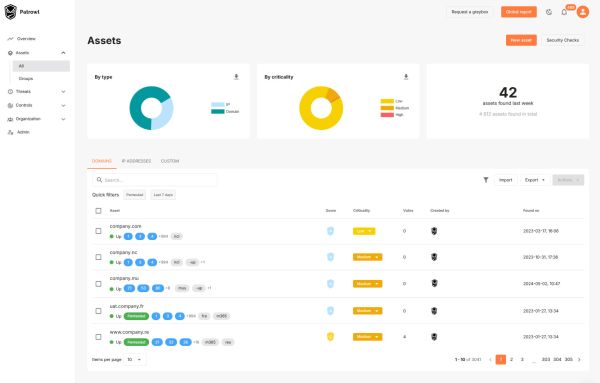
Organize and Enrich Your Inventory
What it does:
Centralizes all discovered assets in one dashboard with enriched asset information (status, technology, criticality, owner). Create dynamic groups for clear management.
What you get:
- Instant visibility by team, perimeter, or infrastructure type
- Risk-based sorting for easier vulnerability management
- Exportable formats (PDF, CSV) and integration with your management systems (CMDB, SIEM, ITSM)
Run Security Checks Continuously
What it does:
Launch automated tests on exposed assets to detect known vulnerabilities, misconfigurations, or outdated software.
What you get:
- Prioritized results, with no noise or false positives
- Clear remediation steps and reduced manual audit costs
- Supports ISO 27001, DORA, NIS2, and more

Get Actionable Technical Data
What it does:
Captures rich, real-world asset data — HTTP headers, SSL certs, tech stack, exposed services — for each discovered asset.
What you get:
- Clear risk context to support fast, informed decisions
- Full traceability of asset evolution and incidents
- Structured asset data aligned with your IT and security workflows

Integrate Easily and Scale Without Friction
What it does:
Patrowl is fully agentless. Connect it to your stack via open API, integrate with workflows, or export as needed.
What you get:
- Instant, no-risk setup (nothing to install)
- API-driven automation across your CI/CD, ticketing, and management tools
- Works seamlessly across distributed teams and environments





Who Uses Patrowl?
CISOs & Security Managers
Stay compliant and reduce blind spots with always-on asset visibility.SOC Teams
Use real exposure data to reduce alert fatigue and target real threats.Risk & Compliance Officers
Produce audit-ready reports and maintain proof of continuous monitoring.IT Leaders & Architects
Sync exposed assets into your CMDB, CI/CD pipelines, or management systems.Organizations of Any Size
Whether you're an SMB or enterprise, Patrowl fits your resources and scales with you.

Our Partenerships
A Recognized Cybersecurity Platform
Winner – InCyber Europe Grand Prix (FIC) 2025
Innovation Award – Les Assises de la Cybersécurité
France Cybersecurity Label
100% renewal rate in 2024
Featured in Wavestone’s Cybersecurity Radar

Our Offers
Anticipate attacks before they happen. Move from one-off testing to continuous security monitoring.
Advanced EASM
Take control of your attack surface.
Real-time, continuous monitoring of all exposed assets (domains, certificates, applications, emails, credentials)
Immediate detection of Shadow IT, misconfigured services, and forgotten assets
Risk-based prioritization of exposures, using active threat intelligence (CISA KEV)
Rapid reduction of your attack surface through automated, guided remediation
Full visibility into what’s publicly accessible — no blind spots, no surprises
Continuous Pentest
Automate your pentests, identify real vulnerabilities.
Real-time, dynamic mapping of your external attack surface
Automated pentests validated by certified experts — zero false positives
Continuous testing of applications, exposed services, ports, protocols, and subdomains
Prioritization of vulnerabilities based on business impact and exploitability
Expert remediation reports with clear, actionable fixes for fast response
Frequently Asked Questions (FAQ)
How does Patrowl's asset discovery work?
It combines passive and active discovery methods (DNS scans, TLS checks, banner grabbing, etc.) to uncover assets across cloud providers, virtual machines, and external services.
What asset information is collected?
Each asset includes metadata like IP, domain, port, service, certificate, tech stack, exposure level, and ownership. This collected data supports risk analysis and response.
Can I connect Patrowl to my management systems?
Yes. Use our REST API to sync with CMDBs, ticketing tools, CI/CD pipelines, and SIEMs — supporting both management and security needs.
Can it detect virtual machines and cloud-based assets?
Yes. It finds any internet-exposed asset, including cloud instances, VMs, and ephemeral environments spun up during deployments.
How does Patrowl help with vulnerability management?
It runs continuous tests, detects known CVEs and misconfigurations, then ranks issues by risk — giving you clear steps to remediate quickly.
Is Patrowl audit- and compliance-ready?
Yes. You can generate scoped reports (PDF/CSV), track remediation, and meet standards like ISO 27001, NIS2, and DORA.