Platform
14 November 2025 CVE Florent Montel
FortiThing, a classic Friday

You like this content ?
Share it on the networks
Yet another classic Friday morning at Fortinet’s office.
A quiet Fortinet patch release drops (https://docs.fortinet.com/document/fortiweb/8.0.2/release-notes/91537/resolved-issues), a tweet from Defused indicating a new exploitation used by attacker (https://x.com/defusedcyber/status/1975242250373517373), and suddenly everyone realizes there’s again a new massive Fortinet problem.
But of course, still no CVE, no official details, and no clear guidance from Fortinet (no CVE, no PSIRT yet at the time writing the article, nothing). And again first question every security team asks is always the same:
“Do we have any FortiWeb instances exposed? Am i Vulnerable?”
UPDATE : 11/14/2025 6PM: Fortinet has, at last, relased the related security bulletin (24h after the whole internet, well done !)
https://fortiguard.fortinet.com/psirt/FG-IR-25-910
As planned, it’s critical, as planned, it’s on FortiWeb, and as planned, it is late.
For most organizations, the honest answer is: nobody knows for sure. Do you even know that the product FortiWeb exists? Real question.
The list in Fortinet’s product portfolio is never ending : FortiWeb, FortiGate, FortiProxy, FortiCASB, FortiManager, FortiAnalyzer, FortiNAC, FortiMail, FortiSIEM, FortiSandbox, FortiVoice (?!)… Each product has multiple major versions, minors, patches, and hotfixes. They all have their own web interfaces, their own FortiOS version, their own administrative interfaces/port.
How do you avoid scrambling every time a new critical Fortinet vulnerability appears : when all you have at first is a tweet, a few unverified GitHub exploits, and a flood of rushed blog posts?
Pragmatism and reflexion
Every article that will pop today will be detailing the exploitation path, which is in fact a simple web request on the interface that could be easily retrieved from the original Tweet from Defused.
The exploitation code has been tested on our lab and is effectively working on version 8.0.1 version of Fortiweb, and patched and version 8.0.2. No need for specific python Github exploit, even a simple curl request is working pretty well.
But, of course, publishing and launching the exploitation code massively is clearly not the best idea that we could have. Instead of thinking like an attacker, maybe it’s time to think as EASM professionals and search for the real valuable data in this kind of situation > do I have a bloody FortiWeb interface exposed on internet?
And, the answer is in fact pretty simple to answer. Luckily, Fortinet loves to name all their products, but they also love to name their interfaces with the name of the product.
A Fortiweb interface is quite easy to detect:
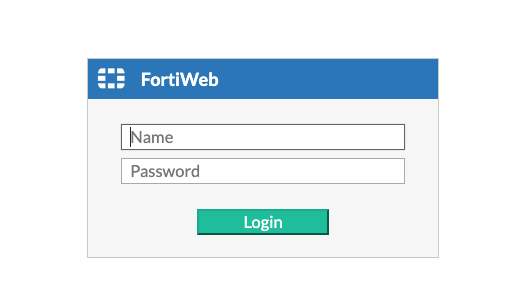
Then, by using curl, python, nuclei, or whenever language you want to use, the detection is quite simple.
Here is a basic example of a nuclei template helping the detection:
id: fortiweb-login
info:
name: Fortinet FortiWeb Administrative Panel
author: Patrowl
severity: high
description: FortiWeb is a web application firewall (WAF) developed by Fortinet. It is designed to protect web applications from various cyber threats, including SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and other types of web-based attacks. FortiWeb helps organizations secure their web applications and prevent unauthorized access or exploitation of vulnerabilities.
http:
- method: GET
path:
- "{{BaseURL}}"
matchers-condition: and
matchers:
- type: word
part: body
words:
- "Please login"
- "ftnt-fortinet-grid"
- "FortiWeb"
condition: and
- type: status
status:
- 200
# digest: 4a0a00473045022078d78e0fe2b60f943dc1a79d5a1ab0991da088729caa5f25be136f66278bd38c022100a8b736886aacbec3514c70e9c3820ef050eea4047cfd38043f7ff428afb536e6:922c64590222798bb761d5b6d8e72950Simple as that. Detecting this precise interface will allow you to clearly prioritize your work and your patching. Instead of lying on a maybe unstable and impacting exploitation code (creating an administrator user is not insignificant), you can use this to detect the real impacted product on your external (or even internal) surface.
You can also use Shodan to search for IP belonging to your infrastructure with a basic filter:
Patrowl, of course.
And yes, the obvious answer to all Fortinet problems you expect from me is simple: just subscribe to Patrowl.
Because while everyone else is panicking over a tweet, unverified GitHub PoCs, and dozens of low-quality “breaking news” articles, our customers were already warned.
Patrowl automatically:
Detects all exposed Fortinet products
Identifies all FortiWeb instances with very high precision
Recognizes 40+ different Fortinet interface patterns in our Risk Insights engine
Alerts customers instantly when a new vulnerability matches their exposure
Validates risks internally in a controlled way to confirm whether they’re affected
So while others are still asking, “Do we even run FortiWeb somewhere?”, our customers already know — clearly, instantly, and without stress.





