Here are some comments acting as conclusions, mostly related to the responses on the Vosges gendarmerie tweets.
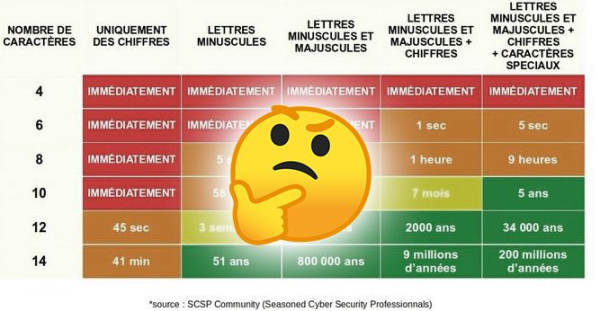
Going back to the gendarmerie board and my introductory example, if a 12-character password is in a dictionary, then it's easy to break.
Just as a 9-character password can be difficult to break, if it is really complex (with a high entropy). So everything will depend on the information available to the attacker and the context.
No, not if this password is in a dictionary and thanks for the idea, I'm adding it to my own dictionaries (at least the "CM#Apollon" because the year will be added by my derivation rules)
Yes yes yes!
Re-yes yes yes!
No, an attacker won't be able to guess your password and authenticate for you on Axa or Facebook in 2 minutes, even if your password is 8 lowercase and uppercase (unless he already has your password).
Here is Mitnick's video showing how to break a complex password in less than a minute: https://www.youtube.com/watch?v=46ODE0bot1I&feature=youtu.be
It generates a password that looks strong but in reality it is not, then it uses the hashcat tool with a dictionary (not provided) and derivation rules (not provided).
This password is written in "leet speak", that is to say by replacing some characters by numbers (cf. wikipedia), a known technique and the hashcat tool embeds adapted derivation rules allowing to transform, for example, "password" in "p4ssw0rd". Then, as the dictionary and the derivation rules are not provided, it is impossible to know if this password (at least partially) is not already in its dictionary. The same is true for the derivation rules which are perhaps specifically adapted to this demonstration 😉.
And no, using the same password with the site name is not a good idea. If an attacker looks at your case manually, it will be obvious for him to find your other passwords.
And no, the tools mentioned (here Cellebrite) mainly use vulnerabilities (or protection bypass techniques) to get into the devices and most often require physical access (I'm not going to talk about iCloud attack tools like Elcomsoft's here).
The best recommendation is to have a password vault (Keepass, Bitwarden, Dashlane...) with complex (randomly generated) and unique passwords per site/service, combined with a strong two-factor authentication.